Cyber & data security shields your digital assets from unauthorized access, breaches, and malicious activities. By implementing robust measures such as encryption, firewalls, and regular audits, it ensures the protection of sensitive information and fortifies your digital infrastructure against evolving cyber threats.
Services
ENDPOINT
- K7 On-premises Endpoint Security
- K7 Cloud Endpoint Security
- K7 Endpoint Security for Operational Technology
NETWORK SECURITY
- K7 Next Generation Firewall
- K7 VPN Concentrator
- K7 Connect 500
- K7 SD-WAN
AUDIT & TESTING
- OSINT
- VAPT
Endpoint
K7 Enterprise Endpoint Security
Advanced multi-layered security provides comprehensive protection against digital threats with the scalability and manageability that is required for enterprise-wide deployments.
K7 On-Premises Enterprise Endpoint Security
Highly scalable, on-premises enterprise endpoint protection with granular and centralised control over applications, devices, and networks.
K7 Endpoint Security (K7 EPS) anticipates, detects, and blocks cyberthreats, ensuring uninterrupted operations and protecting confidential business information. Designed to satisfy the needs of the modern enterprise, EPS scales to protect any size of business operations, does not need an extensive in-house IT team to be deployed rapidly, and is available in Standard and Advanced editions.


K7 Cloud Endpoint Security for the Enterprise
Rapid enterprise-wide deployment with anytime, anywhere control over applications, devices, and networks
The modern enterprise has employees working anywhere and everywhere – in office, on-site, or working from home. K7 Cloud Endpoint Security (K7 CEPS) is the easiest way to protect and manage all enterprise endpoints in an environment without a clear IT perimeter. Knowledgeable and proactive customer support ensures that cybersecurity never gets in the way of 24/7 operations.
K7 Endpoint Security for Operational Technology
Enterprise-grade malware protection for manufacturing processes, with minimal resource consumption
K7 Endpoint Security for Operational Technology (K7 EPS OT) provides multi-layered cyberattack protection for endpoints used in production plants. K7 EPS OT is designed to work with the resource-intensive industrial control solutions, modest hardware, and legacy platforms found in Oil & Gas and other must-run security-sensitive industries.

K7 Network Security
K7 Security’s Network Security devices enable gateway security and secure communication between branches, headquarters, and the cloud.
1. K7 Next Generation Firewall
High performance gateway security hardware with AAA framework integration
The K7 Next Generation Firewall (K7 NGFW) range of devices provide hardened network security to stop cyberthreats, including denial of service (DOS) attacks, with gateway-level malware protection to enable cost-effective creation of robust and resilient enterprise networks.

3 DIFFERENT SERIES

K7 A-Series

K7 S-Series

K7 M-Series
Ports: 8
Users: 100-550
Concurrent Sessions: 6,200,000-21,000,000
Highlights
SPI Firewall
Enterprise-Class Network Features
VPN
SSL based secure connections between IPSec gateways, Static IP and Dynamic IP configurations
AAA Framework
Web Security
Logging & Reporting
35+ Live Logs, 40 different report formats help with compliance reporting, diagnosing network issues
2. K7 VPN Concentrator
Cost-effective high performance VPN Infrastructure for Head Offices
Conventional VPN solutions struggle to support the widely distributed enterprise with a large number of users and locations. The K7 VPN Concentrator enables cost-effective and secure connectivity between headquarters, branch offices, data centers, and remote workers. Multiple VPN tunnels that work with any ISP ensure secure remote access for up to hundreds of users.

Highlights
Multiple virtual VPN servers
Load balance & ILLB
Works with all ISP links
Auto Failover of VPN tunnels
Remote Manageability
SLA Monitoring
3. K7 Connect 500
Cost-effective Secure Connectivity Appliances for Small Branch Offices
The modern enterprise needs to provide high bandwidth and low latency connectivity for users across a large number of small offices. Avoid the high costs, poor reliability, and impaired productivity of conventional private WAN with the K7 Connect 500 range of Secure Branch Connectivity devices.
The K7 Connect 500 devices are the first to integrate mobile internet with built-in SIM support in addition to other connectivity options, enabling satellite facilities to connect by leveraging the most reliable internet network available at their site.

Highlights
Works with Local, Public IP and any ISP
Network Failover and Security
Active-Active Load Balancing
Failover between VPN and ISP
Auto Failover between ISP/USB/SIM
Remote Management and Secure Remote Access
4. K7 SD-WAN
High-performance SD-WAN using any ISP
Router-centric WAN architecture struggles to manage the network demands of enterprises that combine distributed operations with on-premises data centres, public or private clouds, and SaaS services. K7 SD-WAN delivers optimised routing to improve application performance and user productivity while reducing operational costs and prevents network downtime.
Highlights
Works with All ISP Links
Seamless and Secure Remote Access to CRM/ERP software
100% Uptime between HQ and Branch
Remote Manageability
Multiple Virtual VPN Servers
SLA Management
CyberSecurity Audit
2 types of tests : OSINT and VAPT
VAPT: Enterprise Vulnerability Assessment & Penetration Testing to Strengthen Cyber Security and Ensure Regulatory Compliance
Maintaining enterprise cyber security requires proactive investigation to identify security gaps and close them before they are exploited by threat actors, which is beyond the mandate of internal IT teams. Vulnerability Assessment and Penetration Testing (VAPT) can provide investigative analysis, but conventional VAPT providers often only use software tools to conduct an audit and generate a report. This approach provides a superficial evaluation of an organisation’s IT ecosystem, does not identify all potential enterprise vulnerabilities, and the report does not highlight areas of concern that must be addressed immediately.
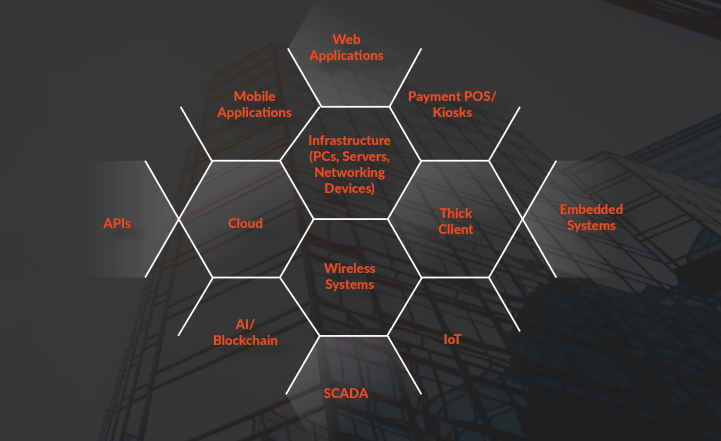
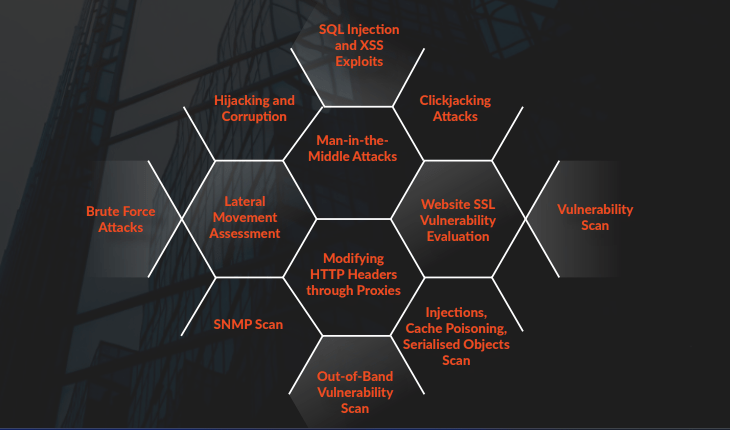
K7’s team perform white hat hacker attacks on systems from both within and outside the enterprise for a comprehensive security evaluation of the various elements that comprise enterprise IT ecosystems.
K7’s experts employ attack utilities and the Tactics, Techniques, and Procedures (TTPs) used by threat actors to test the organisation’s resilience against a broad gamut of cyber threats.
